This is a cautionary tale, at the risk of embarrassing myself. I did not even know what ‘ransomware’ was until it infected my computer. This article is not a definitive piece on how to protect yourself from a virus. The main message is don’t do as I did.
Ransomware is a type of malware that prevents access to computer files until the victim pays a ransom to regain access or retrieve the data.
How was I tricked?
Let’s start at the beginning to at least give me some excuses. I had been exchanging emails and phone calls with Telstra, as part of a significant upgrade to faster broadband speed, higher data allowance and upgraded mobile phone plan. In my defence, my head was in a ‘Telstra numbers' mode, full of megabytes and download speeds.
Then a few days after my upgrade, I received an email, supposedly from Telstra Customer Care, telling me I was over 50% of my monthly data allocation, with a link to my usage level. How could that be? I had only just changed to the new package. Immediately preparing myself to call Telstra and tell them to get their act together, that they had me on the wrong plan, I clicked on the link to check the numbers. Bad mistake, a strike at my soft underbelly.
The email was not from Telstra. This message jumped up on my screen.
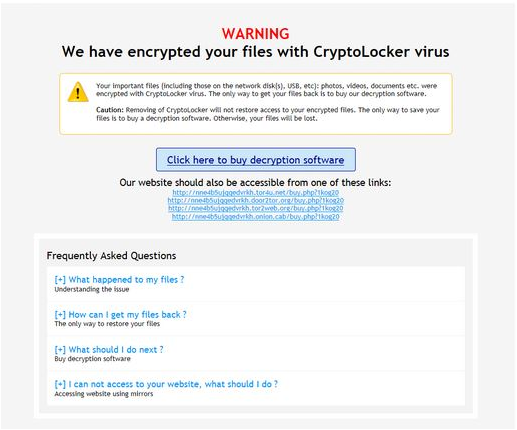
It was a ransomware virus called CryptoLocker. Google it if you want to know more. It works by encrypting all the files on your computer, and to unlock or decrypt them, you pay a 'ransom' to receive a decryption key. I immediately removed the virus but it was too late. All my files – Word, Excel, PowerPoint presentations, photographs, videos – were encrypted and could not be opened. The ransom requested was GBP700, payable in Bitcoins. They said if I tried to remove the virus, it would not decrypt the files and the cost of the key would increase to GBP1,400.
Searching online for a solution, some people suggested there is a publicly available key to decrypt the files, but this is a public key used by other malware scams. My understanding is CryptoLocker uses two keys: one to encrypt and another to decrypt the data. The decryption key is a private key, which is not available other than by paying the ransom.
What about my backup?
I immediately contacted my technical support, who said this was a particularly nasty virus, and industry advice is not to pay the ransom as most people do not receive the decryption code after payment. An online search confirmed this, while others said they did not want to encourage criminals by paying the ransom. It was better to rebuild from backups.
Where were my backups? This is the embarrassing bit.
First, we tried ‘System Restore’, which if enabled on the computer, should hold shadow copies of files. But when we clicked on ‘Previous Versions’, nothing was there.
Second, what about back-ups to external hard drives? I had been told some months earlier that there are only two types of external hard drives: those that have stopped working, and those that are about to stop working. A company called Backblaze, which runs 25,000 external hard drives continuously in its backup business, reports a 5% fail in the first 18 months, and 22% in four years. No doubt this is unfair, but I used it as an excuse not to back up to external hard drives more regularly.
Third, my computer had been set up to copy files regularly to Dropbox. When I went into my Dropbox account, the files there were also encrypted. So I wrote to Dropbox asking if they had saved previous versions. There ensued an exchange of emails with Dropbox, such as:
“I'd be happy to help you roll back your entire account to a certain point in time. Could you go to https://www.dropbox.com/events and send me the link indicating the first event you would like to undo? Your account will be reverted to before this event took place.”
But over many exchanges of email, we could not open my old files. I don’t blame Dropbox for this, we just ran out of time and patience.
So where did I eventually find some of the lost files? I had older files on an external hard drive from my last (too long ago) back up. Otherwise, I retrieved wanted files that had been attached to emails: photographs, documents, spreadsheets. I recovered a decent amount stored by Google on Gmail (and it would be the same with any reputable email service) and all Cuffelinks files are ‘in the cloud’.
But I did lose a lot of personal material. I had copied photographs to my computer from my iPhone to free space on the phone. Other personal records, documents and spreadsheets, were lost.
What are the lessons?
All it takes is one email from a trusted friend or a familiar company, complete with logo and well-designed customer letter, plus a moment’s lack of the usual caution and this could happen to you. The lessons are:
- Always pause before opening a link, regardless of who it is from, and make sure it is legitimate. Hackers have ways of accessing your contacts and companies you deal with.
- Back up to an external hard drive regularly, but make frequent checks and hardware upgrades.
- Store additional copies in the ‘cloud’.
- Activate the programme which stores shadow copies.
- Email important documents to yourself. From my experience, this is a robust solution, and if anyone thinks it is not, let me know.
Repeating, I am not a technical expert on this subject, and I welcome comments from people who know a lot more than I do. Including the best ways to back up (no product flogs, please).
Comment by Tony Cuffe who works in technical support
This type of invasive software is, unfortunately, becoming more and more common. It opens up a lot of discussion as to how to avoid it in the future. Backing up properly is a form of risk management.
For Mac users I suggest that an Apple Time Machine is installed as well as using a programme such as Carbon Copy to do remote backups of valuable files such as photos and documents on a regular basis to remote drives. These can be setup to run automatically in the background.
For Windows users this is not so simple. There are a range of different solutions from different suppliers. One that seems pretty good is from Acronis. They do both automatic updates to local remote drives and also the cloud.
Speaking of cloud, we are now primarily using Google Drive along with the full suite of Google apps for work applications. This means that all files are being kept in the cloud and are not touchable with programmes like CryptoLocker. We are currently retiring our laptops and replacing with them with Chromebooks. The only thing needed is an internet connection via wi-fi and you have everything available.
Finally, as for email, using a hosted cloud service such as Apple iCloud or Google Gmail is the only way to go as you can easily re-download your email to any device whether it be Windows, Apple or Linux. I use both for different email addresses but my first choice is now Gmail and particularly Gmail for business so you can set up your own domain name for your email address.
Graham Hand is Editor of Cuffelinks. This article is a general warning and does not consider the personal circumstances of any readers, nor is it intended as a definitive solution to protecting data and files.